NSA targets the privacy-conscious
One of NSA's German targets is 212.212.245.170. The string of numbers is an IP address assigned to Sebastian Hahn, a computer science student at the University of Erlangen. Hahn operates the server out of a grey high-security building a few kilometers from where he lives. Hahn, 28 years old and sporting a red beard, volunteers for the Tor Project in his free time. He is especially trusted by the Tor community, as his server is not just a node, it is a so-called Directory Authority. There are nine of these worldwide, and they are central to the Tor Network, as they contain an index of all Tor nodes. A user's traffic is automatically directed to one of the directory authorities to download the newest list of Tor relays generated each hour.
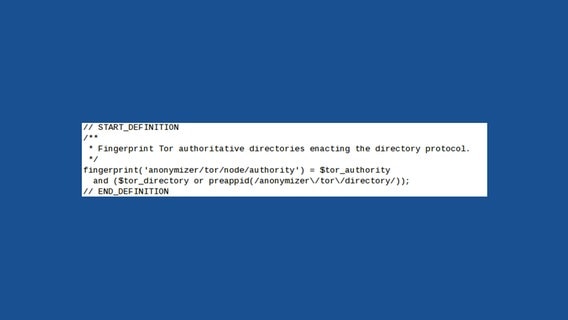
Hahn's predecessor named the server Gabelmoo, or Fork Man, the nickname of a local statue of Poseidon. After a look at the NSA source code, Hahn quickly found his server's name listed in the XKeyscore rules. "Yes, I recognize the IP address of my Tor server called 'gabelmoo'." he said. "Millions of people use it to stay safe online, and by watching the server and collecting metadata about its users, those people are put at risk." The rule shown to Hahn, published below, has a fingerprint called 'anonymizer/tor/node/authority'. The fingerprint targets users who connect to Gabelmoo and other Tor Directory Authority servers. In Germany, the Tor Directory Authorities like Gabelmoo that are specifically targeted by XKeyscore rules are in Berlin and Nuremberg. Additional targets are located in Austria, Sweden, the United States, and the Netherlands.
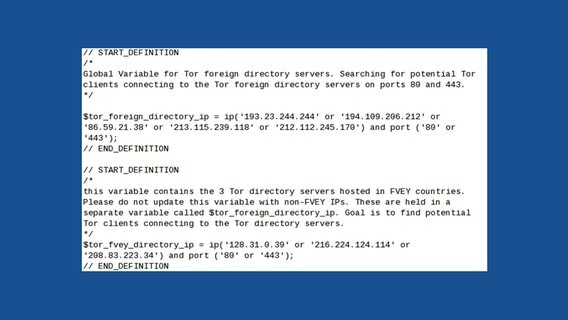
The expression below performs essentially the same function, but it specifies the Tor directory authorities located in Five Eyes countries (Australia, Canada, New Zealand, the United Kingdom and the United States) separately from those in other countries. As the comment explains, the "goal is to find potential Tor clients connecting to the Tor directory servers."
Another rule catalogs users connecting to known Tor relays. This is not difficult, because the addresses of all normal Tor relays are published by the directory authorities so that the Tor software on users' computers can select its own path through the network. In addition to the public relays, connections characterized as Tor based on protocol identifiers are also cataloged.
Not only Metadata
Internet service providers in countries with strong censorship such as China and Iran frequently block connections to known Tor relays. To avoid this blocking, The Tor Project maintains a list of non-public relays called "bridges" to allow users to avoid this type of blocking. Bridges are run by volunteers and they share the details with the Tor Project to help censored users reach the internet.
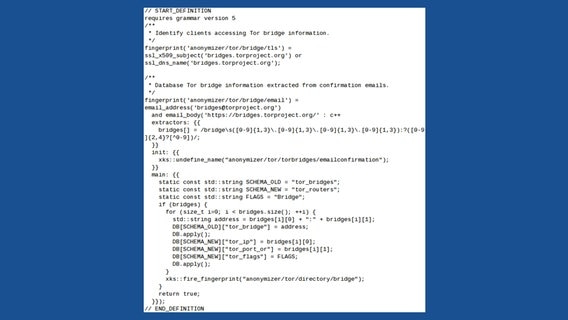
Users can request a bridge address via email or on the web. The following fingerprints show two ways that XKeyscore attempts to track Tor bridge users. First, the fingerprint "anonymizer/tor/bridge/tls" records connections to the bridges.torproject.org server. Second, in order obtain the actual bridge addresses for the purpose of tracking connections to them in the future, the "microplugin" fingerprint called "anonymizer/tor/bridge/email" extracts data from the body of the emails that the Tor Project sends to its users.
This code demonstrates the ease with which an XKeyscore rule can analyze the full content of intercepted connections. The fingerprint first checks every message using the "email_address" function to see if the message is to or from "bridges@torproject.org". Next, if the address matched, it uses the "email_body" function to search the full content of the email for a particular piece of text - in this case, "https://bridges.torproject.org/". If the "email_body" function finds what it is looking for, it passes the full email text to a C++ program which extracts the bridge addresses and stores them in a database.
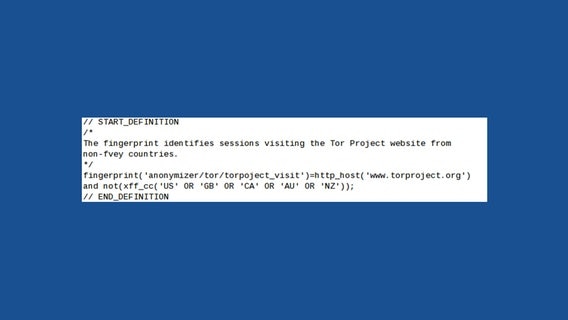
The full content of the email must already be intercepted before this code can analyze it. XKeyscore also keeps track of people who are not using Tor, but who are merely visiting The Tor Project's website (www.torproject.org), as this rule demonstrates:
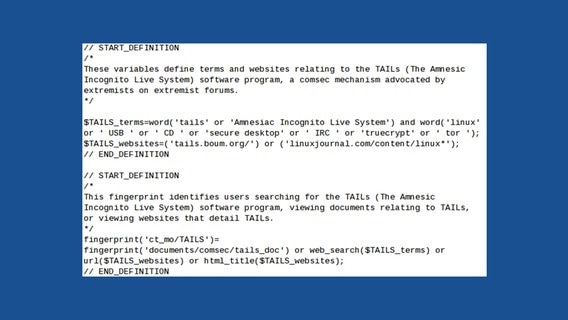
It is interesting to note that this rule specifically avoids fingerprinting users believed to be located in Five Eyes countries, while other rules make no such distinction. For instance, the following fingerprint targets users visiting the Tails and Linux Journal websites, or performing certain web searches related to Tails, and makes no distinction about the country of the user.
The comment in the source code above describes Tails as "a comsec mechanism advocated by extremists on extremist forums". In actuality, the software is used by journalists, human rights activists, and hundreds of thousands of ordinary people who merely wish to protect their privacy.